Two Factor Authentication - 2FA: Difference between revisions
| (2 intermediate revisions by the same user not shown) | |||
| Line 1: | Line 1: | ||
== Activate 2FA == | == Activate 2FA == | ||
To activate two-factor authentication (2FA), you can edit the configuration within nuBuilder under '''Setup -> Settings'''. | |||
Alternatively, you can edit the following settings directly in the '''nuconfig.php''' file. | |||
By default, these options are disabled. | |||
<pre> | <pre> | ||
$nuConfig2FAAdmin = false; //-- | $nuConfig2FAAdmin = false; //-- Enable 2FA for administrators | ||
$nuConfig2FAUser = false; //-- | $nuConfig2FAUser = false; //-- Enable 2FA for users | ||
$nuConfig2FAFormID = "nuauthentication"; //-- 2FA form ID | $nuConfig2FAFormID = "nuauthentication"; //-- 2FA form ID (default: nuauthentication) | ||
$nuConfig2FATokenValidityTime = 168; //-- | $nuConfig2FATokenValidityTime = 168; //-- Token validity period in hours (default: 7 days) | ||
$nuConfig2FAShowRememberMe = false; //-- Show | $nuConfig2FAShowRememberMe = false; //-- Show "Remember me for X days" checkbox (not yet implemented) | ||
</pre> | </pre> | ||
Additionally, 2FA can be activated or deactivated for individual access levels. | |||
This means if you enable 2FA for general users, you must also enable it for the specific access levels that require this protection. | |||
=== Functionality === | === Functionality === | ||
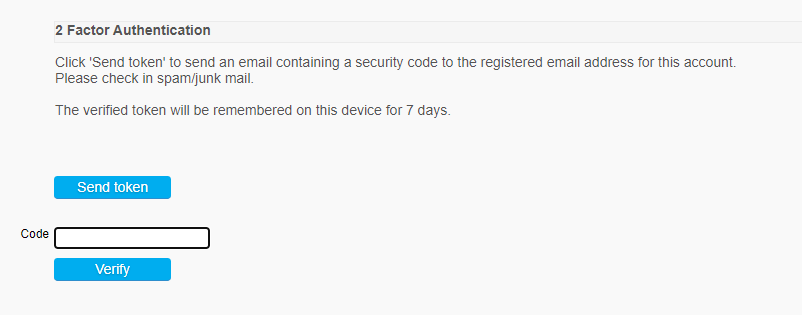
When 2FA is enabled, users are redirected to an authentication form after their initial login. | |||
On this form, users can request a 2FA token, which is sent to them via email or another configured method. | |||
Entering a valid token grants access and redirects the user to their intended destination. | |||
Users cannot access other parts of the application until they have successfully authenticated. | |||
The 2FA session remains valid on the same device and browser for the duration specified by the "Token Validity Time". | |||
[[File:2fa.png]] | [[File:2fa.png]] | ||
| Line 20: | Line 30: | ||
=== Setting up 2FA === | === Setting up 2FA === | ||
Navigate to '''Home -> Builders -> PHP Procedure "nu_authentication_2fa_template"''' | |||
Clone the template. The procedure code will automatically be renamed to nu_authentication_2fa. | |||
Adapt the PHP code as needed and save it. | |||
=== Define Save IP Addresses === | |||
You can define a set of "safe" IP addresses to bypass the 2FA requirement for users on trusted networks. | |||
If a user connects from one of these whitelisted IP addresses, the two-factor authentication step will be skipped. | |||
This feature supports both IPv4 and IPv6 addresses, including wildcard patterns (e.g. 192.168.*.*, 10.0.0.1, 2001:db8::/32). | |||
Safe IPs are defined in the following configuration structure in '''nuconfig.php''': | |||
For both globeadmin and users, you can define one or more IP addresses that are exempt from 2FA. | |||
Sample configuration: | |||
<pre> | <pre> | ||
$ | $nuConfig2FASafeIPAddresses = [ | ||
'globeadmin' => [ | |||
'192.168.1.10', // Office main server | |||
'192.168.1.11', // Admin workstation | |||
'203.0.113.50', // Remote admin VPN | |||
'::1' | |||
], | |||
'user' => [ | |||
'*' => [ // Applies to ALL users | |||
'203.0.113.200', // Corporate VPN | |||
'198.51.100.100', // Office network | |||
'::1' | |||
] | |||
] | |||
]; | |||
</pre> | </pre> | ||
Latest revision as of 13:59, 9 August 2025
Activate 2FA
To activate two-factor authentication (2FA), you can edit the configuration within nuBuilder under Setup -> Settings.
Alternatively, you can edit the following settings directly in the nuconfig.php file.
By default, these options are disabled.
$nuConfig2FAAdmin = false; //-- Enable 2FA for administrators $nuConfig2FAUser = false; //-- Enable 2FA for users $nuConfig2FAFormID = "nuauthentication"; //-- 2FA form ID (default: nuauthentication) $nuConfig2FATokenValidityTime = 168; //-- Token validity period in hours (default: 7 days) $nuConfig2FAShowRememberMe = false; //-- Show "Remember me for X days" checkbox (not yet implemented)
Additionally, 2FA can be activated or deactivated for individual access levels. This means if you enable 2FA for general users, you must also enable it for the specific access levels that require this protection.
Functionality
When 2FA is enabled, users are redirected to an authentication form after their initial login. On this form, users can request a 2FA token, which is sent to them via email or another configured method.
Entering a valid token grants access and redirects the user to their intended destination. Users cannot access other parts of the application until they have successfully authenticated. The 2FA session remains valid on the same device and browser for the duration specified by the "Token Validity Time".
Setting up 2FA
Navigate to Home -> Builders -> PHP Procedure "nu_authentication_2fa_template"
Clone the template. The procedure code will automatically be renamed to nu_authentication_2fa.
Adapt the PHP code as needed and save it.
Define Save IP Addresses
You can define a set of "safe" IP addresses to bypass the 2FA requirement for users on trusted networks. If a user connects from one of these whitelisted IP addresses, the two-factor authentication step will be skipped.
This feature supports both IPv4 and IPv6 addresses, including wildcard patterns (e.g. 192.168.*.*, 10.0.0.1, 2001:db8::/32).
Safe IPs are defined in the following configuration structure in nuconfig.php: For both globeadmin and users, you can define one or more IP addresses that are exempt from 2FA.
Sample configuration:
$nuConfig2FASafeIPAddresses = [
'globeadmin' => [
'192.168.1.10', // Office main server
'192.168.1.11', // Admin workstation
'203.0.113.50', // Remote admin VPN
'::1'
],
'user' => [
'*' => [ // Applies to ALL users
'203.0.113.200', // Corporate VPN
'198.51.100.100', // Office network
'::1'
]
]
];